zANTI is a penetration testing toolkit developed by Zimperium Mobile Security for cyber security professionals. Basically, it allows you to simulate malicious attacks on a network. With the help of zANTI, you will be able to perform various types of operations such as MITM attacks, MAC address spoofing, scanning, password auditing, vulnerability checks and much more. In short, this android toolkit is a perfect companion of hackers.
Features:
- Change a device’s MAC address
- Hijack HTTP sessions and Modify HTTP requests and responses
- Exploit Routers
- perform MITM (man in the middle) Attacks
- Capture downloads
- Audit Passwords
Requirements :
- zAnti – Download it from here
- A Rooted Device – Click here to find out how to root your device
Lets Get Started !
Using zAnti :
- Download zAnti from here – Download
- Install it and open it up
- Grant Root Access
- Enter Your email and tick the “I accept Zimperium’s EULA” check box
- Hit “Start Now” button (Next step If you want to join zNetwork, tap on “Enable”, otherwise tap on “Skip”)
- Wait for a Similar following Screen to appear :
- Tap on “Skip” and then enable zANTI (check the “I am fully authorized to perform penetration testings on the network” box) and Hit “Finish” Button
How to Change MAC ?
Mac Changer will allow you to change the MAC address of your WiFi
- Swipe left and Select MAC Changer
How to use zTether ?
This allows you to create a WiFi hotspot and control your network traffic. (Oh yeah)
- swipe to left and choose zTether option
- Turn on “Tether Control” so that users can connect to your network. Once a victim connects to your network then you can play with the traffic.
- You can check out the logged requests by tapping on “View“. Logged requests contain sniffed passwords, sites visited using your network and HTTP sessions. You can tap into any logged activity to get more details (sessions, passwords, requests and user agents)
style="border: 0px; font-family: inherit; font-size: inherit; font-stretch: inherit; font-style: inherit; font-variant: inherit; font-weight: inherit; line-height: inherit; margin: 0px; padding: 0px; text-align: center; vertical-align: baseline;">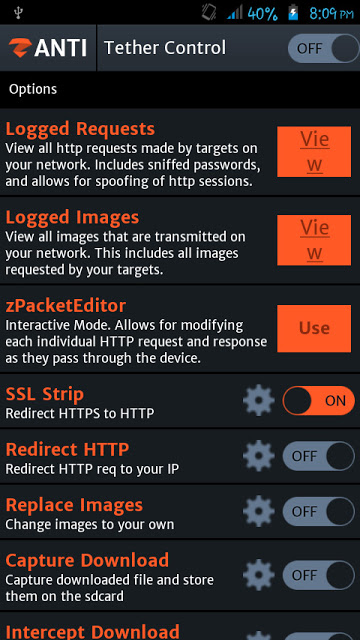

- If you want to hijack the victim’s HTTP session , you can just tap on the session and it will open up the victim’s session.
How to use zPacketEditor ?
It allows you to modify HTTP requests and responses on your network. It is basically an interactive mode that can allow you to edit and send each request and response.
- First, tap on “zPacketEditor” and then turn on the module. You will see the live requests and responses there (1). If you want to edit a particular request or response, swipe it to the right (2). After the edit, you can tap on “Send” button (3).
SSL Strip
SSL Strip is a type of Man In the Middle Attack that forces victim’s browser into using HTTP instead of HTTPS (SSL Strip is turned on by default).
Note: Websites using HSTS (HTTP Strict Transport Security) are immune to SSL Strip attacks.
Moving onto the next one……
Note: Websites using HSTS (HTTP Strict Transport Security) are immune to SSL Strip attacks.
Moving onto the next one……
Redirect HTTP
It allows you to redirect all HTTP traffic to a site or server. For example, If you turn on the “Redirect HTTP”, it will redirect all HTTP traffic to Zimperium servers (default configuration). But if you want to forward all the traffic to a particular site, tap on the settings icon, you will see an area to enter a URL (see the image below). Enter a URL in the field and then again tap on the settings icon.Replace Images
It enables you to replace website images (victim’s web browser) with your own image. In order to replace images:first, tap on the settings icon and then tap on “Select Image”
After selecting an image from your device, tap on the settings icon
Now, the users will see the selected image everywhere on the web!
Capture Download
It allows you to intercept and download all specified files to the SD card. For example, if you want to capture pdf files, you have to tap on the settings icon and then select the .pdf from the menu. Then turn on “Capture Download”.Intercept Download
Intercept Download allows you to replace a downloaded file with a specified file. In order to intercept and replace victim’s downloaded files, you have to tap on the settings icon. Then tap on “Select File” to select a fileInsert HTML
It enables you to insert specified HTML codes into web pages. If you want to display an alert box saying “zANTI Test”, just turn on the “Insert HTML” module. But if you want to insert your own codes into the web pages, you have to tap on the settings icon and then enter your HTML codes. Then tap on settings icon again.How To Scan a Target Device?
First, select a device on your network (just tap on it).
Then tap on “Scan”. You will see the below screen:
You can change the “Scan Type” if you want. You can also run a script while scanning the target, all you have to do is select the required script from the “Execute Script” menu. It also includes a function called “Smart Scanning”, for identifying vulnerabilities of the target device.
After setting the scan options, tap on “Go” to start scanning the device. When the scan completes, zANTI will show a notification as shown below:
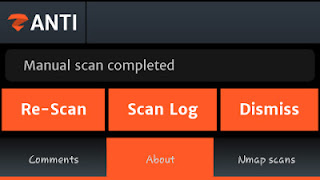
How To Perform MITM Attack?
Performing Man In The Middle attack with the help of zANTI is easier than anything. Follow the below procedures to perform MITM attack:
- Select the target and then tap on “Man in the Middle”. You will see a similar window as in “zTether” (Except the “MITM method”):
MITM Method
The program module named “MITM method” is used to select your favorite MITM technique. Two methods are available: ARP (Address Resolution Protocol) and ICMP (Internet Control Message Protocol).
You may ask “what is the difference between these two methods?” Here is the answer:
ARP MITM attack works by spoofing MAC address within the LAN. That is, the attacker’s machine acts as the target device and router at the same time.
- From the view of the Router – Attackers machine is the user’s machine.
- From the view of victim’s computer – Attackers machine is the router.
ICMP MITM attack works by spoofing an ICMP redirect message to the router. The spoofed message re-routes the victim’s traffic through an attacker-controlled router.






ConversionConversion EmoticonEmoticon